OPSDirectory Audit
This tool detects implementation errors that could lead to security risks.
-
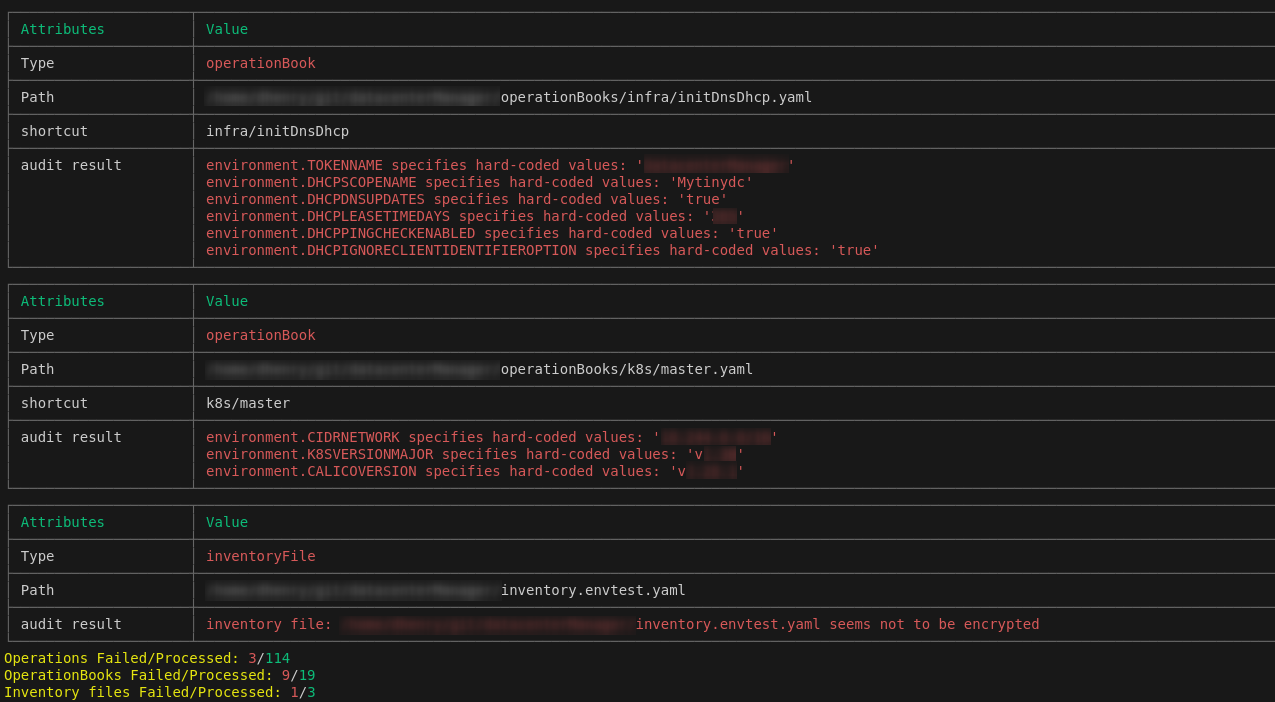
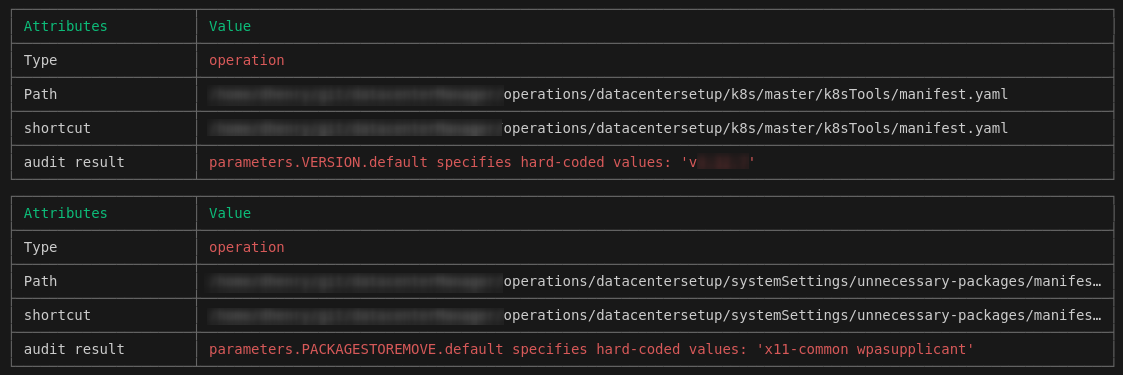
Analyzes “operationBook” and “operation” manifests to detect the use of hard-coded values. These values must be described as
Bashenvironment variables, or as a reference to a value in an inventory file. -
Inventory files must be encrypted.
To run the audit :
OPS="Chemin OPSDirectory" automation-cli audit [options: --help]Sample reports
- Control of variable content in “operationBook” and encryption of inventory files
- Checking variable contents in “operation
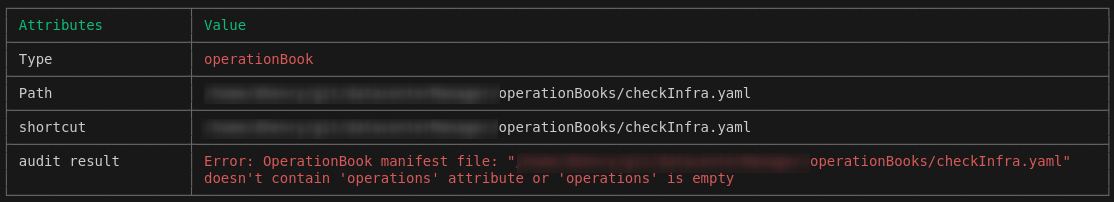
- Control of “operationBook” semantics
The -json switch allows you to obtain the same result in “JSON” format.